How to protect your Mac from Rootpipe
How to protect yourself against the recent Rootpipe vulnerability in the Mac OS X version of sudo, which would allow an attacker total control of your computer.
Read MoreHow to protect yourself against the recent Rootpipe vulnerability in the Mac OS X version of sudo, which would allow an attacker total control of your computer.
Read More In the article below Attorney General Eric Holder said "“It is fully possible to permit law enforcement to do its job while still adequately protecting personal privacy”
In the article below Attorney General Eric Holder said "“It is fully possible to permit law enforcement to do its job while still adequately protecting personal privacy”
This is simply not true, and harkens back to the discredited arguments made by the FBI in the 1990’s about the Clipper Chip. It is hard enough to make secure computing systems, and we are not very good at it as all the breaches demonstrate. Intentionally introducing a vulnerability, which is the essential nature of back door or law enforcement access, is madness. If there is a back door, then keys exist, and can be compromised or reverse engineered. It is an added complexity to the system, which is almost certain to introduce other vulnerabilities. Its use would not be restricted to the US. Once it exists every government will demand access.
Social media and the cloud have tilted the balance of power absurdly towards law enforcement. This argument that they must retain access to encrypted cell phones is fatuous.
Holder urges tech companies to leave device backdoors open for police - The Washington Post
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me on Facebook, Twitter, and Google+.
 Apple is getting taken to task for a couple of security issues.
Apple is getting taken to task for a couple of security issues.
First, their recently announced “Random MAC address” feature does not appear to be as effective as expected. The idea is that the iOS 8 device will use randomly generated MAC addresses to ping WiFi base stations when it is not actively connected to a WiFi network. This allows your phone to identify known networks and to use WiFi for enhanced location information without revealing your identity or allowing you to be tracked. Unfortunately the MAC only changes when the phone is sleeping, which is really rare with all the push notifications happening all the time. The effect is that the “random” MAC addresses are changed relatively infrequently. The feature is still good, but needs some work to be actually very useful.
Second, people are noticing their passwords showing up in Apples iOS 8 predictive keyboard. The keyboard is designed to recognize phrases you type frequently so it can propose them to you as you type, thus speeding message entry. The problem is that passwords often follow user names, and may be typed frequently. Research is suggesting that the problem is from websites that fail to mark their password fields. Apple is smart enough to ignore text in known password fields, but if it does not know that it is a password, then the learning happens. It is not clear that this is Apple’s fault, but it is still a problem for users. Auto-fill using the latest version of 1Password should protect against this.
https://www.youtube.com/watch?v=ceC9jMIpszI
[powerpress]
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me onFacebook, Twitter, and Google+.
 Since it was introduced, Apple has had the ability to decrypt the contents if iPhones and other iOS devices when asked to do so (with a warrant).
Since it was introduced, Apple has had the ability to decrypt the contents if iPhones and other iOS devices when asked to do so (with a warrant).
Apple recently announced that with iOS 8 Apple will no longer be able to do so. Predictably, there has been a roar of outrage from many in law enforcement. [[Insert my usual rant about how recent trends in technology have been massively in favor of law enforcement here]].
This is really about much more than keeping out law enforcement, and I applaud Apple for (finally) taking this step. They have realized what was for Anonymizer a foundational truth. If data is stored and available, it will get out. If Apple has the ability to decrypt phones, then the keys are available within Apple. They could be taken, compromised, compelled, or simply brute forced by opponents unknown. This is why Anonymizer has never kept data on user activity.
Only by ensuring that they can not do so can Apple provide actual security to it customers against the full range of threats, potentially least of which is US law enforcement.
https://www.youtube.com/watch?v=l236gjtzeTc
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me onFacebook, Twitter, and Google+.
 The Internet is on fire with discussions of the recent release of stolen nude photos of over 100 female celebrities. This is a massive invasion of their privacy, and it says something sad about our society that there is an active market for such pictures. While this particular attack was against the famous, most of us have information in the cloud that we would like to stay secret.
The Internet is on fire with discussions of the recent release of stolen nude photos of over 100 female celebrities. This is a massive invasion of their privacy, and it says something sad about our society that there is an active market for such pictures. While this particular attack was against the famous, most of us have information in the cloud that we would like to stay secret.
While there is not a definitive explanation of the breach the current consensus is that it was probably caused by a vulnerability in Apple’s “Find My iPhone” feature. Apparently the API interface to this service did not check for multiple password failures, a standard security practice. This allowed attackers to test effectively unlimited numbers of passwords for each of the accounts they wanted to access.
Because most people use relatively weak passwords, this attack is quite effective. Once they gained access to the accounts, they could sync down photos or any other information stored in iCloud.
Of course, the first rule of secrecy is: If it does not exist, it can’t be discovered.
If you do want to create something that you would be pained to see released publicly, then make sure you keep close control of it. Store it locally, and encrypted.
Wherever you keep it, make sure it has a strong password. Advice for strong passwords has changed over time because of the increasing speed of computers. It used to be that fancy pneumonics would do the trick but now the fundamental truth is: if you can remember it, it is too weak.
This is particularly true because you need to be using completely different passwords for every website. Changing a good password in a simple obvious way for every website is obvious. It might prevent brute force attacks but if some other attack gives access to your password, the attacker will be able to easily guess your password on all other websites.
You need to be using a password manager like 1Password (Mac), LastPass, Dashlane, etc. Let the password manager generate your passwords for you. This is what a good password should look like: wL?7mpEyfpqs#kt9ZKVvR
Obviously I am never going to remember that, but I don’t try. I have one good password that I have taken the time to memorize, and it unlocks the password manager which has everything else.
UPDATE: There appears to be some question about whether this vulnerability is actually to blame.
 In episode 21 of our podcast for July, I talk about:
In episode 21 of our podcast for July, I talk about:
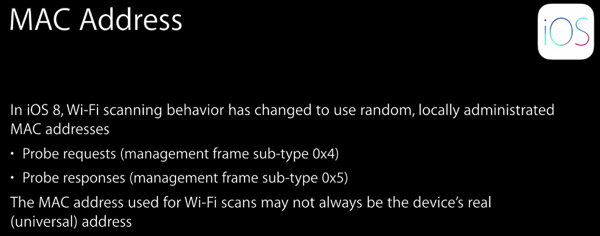
News just broke of a new feature in iOS 8 announced at Apple’s WWDC which was not covered in the big keynote. Advertisers and retail outlets have been using Wi-Fi to track mobile devices for some time. I talked about a network of Wi-Fi tracking trashcans last year in the podcast.
This works because, by default, most mobile devices are constantly on the lookout for Wi-Fi networks. The device communicates with visible base stations to see if they are known, if they are secure, and what they are called. That communication reveals the MAC address of the device’s Wi-Fi.
Like the address on your house, your phone number, or IP addresses, MAC addresses are globally unique identifiers. Everything that can speak Wi-Fi has its own individual MAC address. This makes it a great hook for tracking. If someone sets up a bunch of Wi-Fi base stations, most mobile devices going by will try to connect, giving it their MAC address. By looking at the pattern of those connections, the device can be tracked.
More sophisticated solutions have even used signal strength to triangulate the location of devices within a small area.
The big news is that Apple is going to randomize the MAC addresses of iOS 8 devices when they are probing for networks. If the device were to probe network base stations A, B, and C they would all see different MAC addresses and think that they were tracking different devices. The iPhone or iPad would still use its real MAC when establishing a full connection, but would not provide it to all of the networks it only probes but never actually uses.
This is a really small change which provides significant privacy gains. It is similar to the decision Apple made to use randomized IPv6 addresses by default, rather than ones which uniquely identify the computer or mobile device.
Of course, Apple is also working hard to track us all with iBeacons at the same time….
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me on Facebook, Twitter, and Google+.
 Fake Tor browser for iOS laced with adware, spyware, members warn | Ars Technica
Fake Tor browser for iOS laced with adware, spyware, members warn | Ars Technica
There are a number of different Tor anonymity service apps in the Apple iOS app store. According to several people at Tor, one of them is unofficial and loaded with adware and spyware.
The bad one is "Tor Browser”. If you have it, you should un-install it immediately.
Apple has been requested to remove the app from the store, but no action has been taken so far.
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me on Facebook and Google+.
 Apple Keeps Turning Bluetooth On When You Update Your iPhone
Recent iOS updates have automatically re-enabled Bluetooth for many users who keep it turned off for battery conservation or privacy reasons.
Apple Keeps Turning Bluetooth On When You Update Your iPhone
Recent iOS updates have automatically re-enabled Bluetooth for many users who keep it turned off for battery conservation or privacy reasons.
The increasing use of iBeacons and other Bluetooth based tracking systems make this a bigger privacy worry than before. Tracking via Bluetooth is now a widely and actively used tool in retail and other areas.
Conspiracy theorists suggest that Apple is doing this intentionally to increase the usefulness of iBeacons to track people, and thus encourage their adoption. While this is an appealing idea, the jury is still out on this one.
If you are concerned about this kind of tracking, you can quickly disable Bluetooth in the control center on your iPhone by sweeping up from the bottom of just about any screen and tapping the Bluetooth button. It is fairly easy and convenient to keep Bluetooth turned off most of the time, and just enable it when you want to use a wireless headset or other Bluetooth device for a short while.
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me on Facebook and Google+.
 In episode 17 of The Privacy Blog Podcast for February, 2014 I talk about:
In episode 17 of The Privacy Blog Podcast for February, 2014 I talk about:
 Apple released an update for Mac OS X 10.9 fixing the serious GOTO FAIL SSL vulnerability. This update appears to resolve the problem for The Safari browser, and many other Apple applications that use SSL/TLS.
Apple released an update for Mac OS X 10.9 fixing the serious GOTO FAIL SSL vulnerability. This update appears to resolve the problem for The Safari browser, and many other Apple applications that use SSL/TLS.
If you use a Mac, make sure you install this update ASAP. Go to Software Update and you should see the update available.
 Everybody has been talking about the Apple SSL vulnerability, but just in case you have missed it….
It turns out that for several years Safari has failed to properly check the cryptographic signatures on Server Key Exchanges allowing attackers to mount man in the middle attacks against your browser sessions. Anyone with the ability to intercept your traffic could read and modify the data to or from any secure website you visit (of course they can always do it with insecure websites). This would include any WiFi you are using, the local ISP, backbone ISPs, and government entities wherever you might be, or anywhere along the path yo the server you are trying to reach.
Everybody has been talking about the Apple SSL vulnerability, but just in case you have missed it….
It turns out that for several years Safari has failed to properly check the cryptographic signatures on Server Key Exchanges allowing attackers to mount man in the middle attacks against your browser sessions. Anyone with the ability to intercept your traffic could read and modify the data to or from any secure website you visit (of course they can always do it with insecure websites). This would include any WiFi you are using, the local ISP, backbone ISPs, and government entities wherever you might be, or anywhere along the path yo the server you are trying to reach.
This vulnerability impacts both iOS as well as Mac OS X. You can test whether you are vulnerable here.
There is a patch already available for iOS so update your device now!
If you are on a Mac, switch to using some browser other than Safari. Chrome and Firefox are both safe from this particular attack.
If you are on Windows, Linux, BSD, or Android, you would appear to be safe.