How to protect your Mac from Rootpipe
 Security researcher Emil Kvarnhammar of TrueSec announced the discovery of a new vulnerability in Mac OS X from 10.8.5 though the current 10.10.
Security researcher Emil Kvarnhammar of TrueSec announced the discovery of a new vulnerability in Mac OS X from 10.8.5 though the current 10.10.
The attack is against a unix utility called “sudo” which allows commands to run as the “root” user (which has absolute power on the system). Normally a user with admin privileges needs to type in their password and approve the running of these tasks, but this attack bypasses the user authentication step.
They have not released details on the vulnerability to give Apple time to issue a fix. In the mean time, it looks like you can protect yourself by making your your normal account is not an admin account.
If you are not sure whether your account is an admin account, open System Preferences and click on “Users & Groups”. It will say under your account name whether the account is “Admin” or “Standard”.

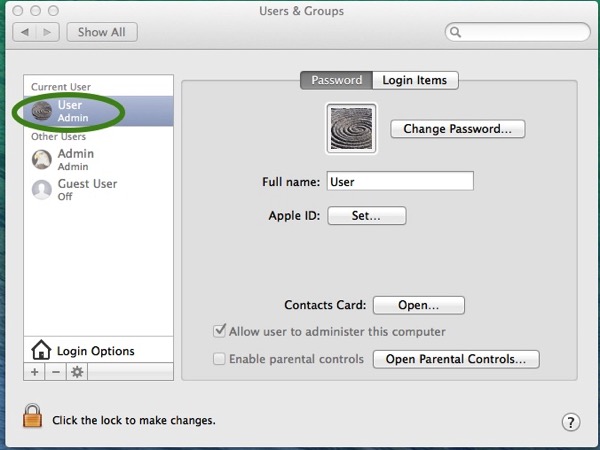 You need to have at least one admin account on the computer. If you are Admin, take the following steps to protect yourself.
You need to have at least one admin account on the computer. If you are Admin, take the following steps to protect yourself.
- If there is no other Admin account on the computer, create a new account by pressing the “+” in the lower left of the list of accounts (you may need to unlock the panel first).
- Log out of your account and log in to the new Admin account.
- As that Admin user, go into the System Preferences / Users & Groups again.
- Click on your normal account and uncheck the “Allow user to administer this computer” checkbox.
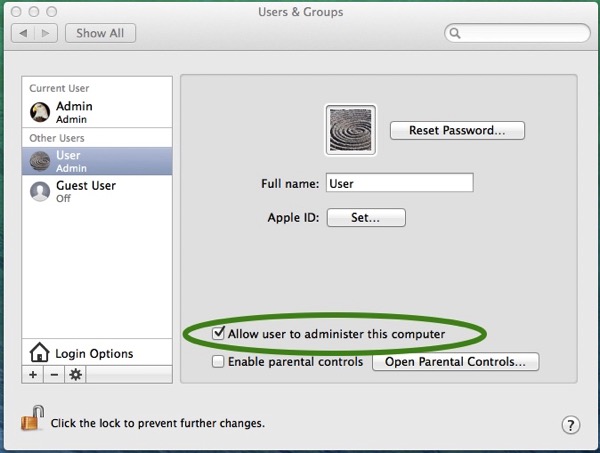
- Log out of the Admin account and log back into your normal account.
TrueSec outlines "Rootpipe" privilege escalation vulnerability in Mac OS X Yosemite
https://www.youtube.com/watch?v=1TWRxZ0Bm9s
[powerpress]
Lance Cottrell is the Founder and Chief Scientist of Anonymizer. Follow me on Facebook, Twitter, and Google+.